In this post I'll present the new Key Derivation Tool I've built, which is being made available for use to the Hive community. Grab a coffee, this is not a particularly short post.
One of the things I like the most about Hive is the possibility to change the private keys of accounts. In the blockchain universe, this is unique to Hive, as far as I'm aware. This mechanic, combined with the system of 4 different, hierarchic keys, offers so much more power and flexibility to the management of an account's security.
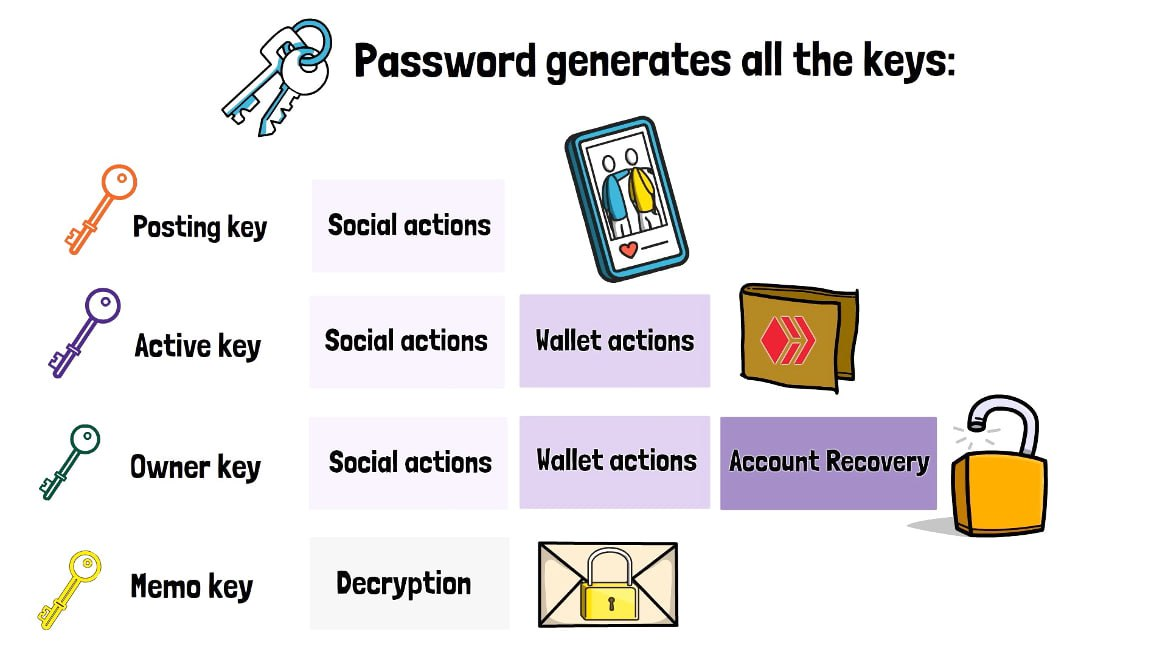
Kudos to the good soul who made this!
However, there's one thing I could never quite accept: in order to change our accounts' keys, we users had to accept that some webpage provides us with a new "master password", from which all 4 key pairs are derived. But how can we be absolutely sure that the new password handed to us has not been logged somehow? Also, having to be online and connected to a website in order to generate new keys always seemed far from ideal.
The change of account keys following this system can be done in the following websites:
Hive Blog - https://wallet.hive.blog/
PeakD - https://peakd.com/
Ecency - https://ecency.com/
Ideally, a user should generate his key pairs offline, and broadcast the "Account Update" (i.e., change of keys) operation exposing only his public keys. Code-wise, this is how an "Account Update" actually works, but the abovementioned websites won't allow users to use their own public keys when changing keys. [Likely to protect users from doing something stupid and end up locking themselves out of their accounts, which is arguably understandable]
Another aspect that deserves consideration is the "traditional" master passwords used by Hive (e.g., by the Hive Wallet website). These are normally 50-character random passwords ("brain keys") prefixed with "P5", like these examples:
P5K4nEpGK6MMvZkgXrNwwGQZv2tTFonkj64cdymUCHqRuMKsLijm
P5JedxCf7TZ7XuQejGbDo8p1dCCxJ7xfLzopLDEmLYRuawDD9ES3
P5JaJcstmZyzzfUQqf4ucpUT4K2ivkLKAn88rnHudUwGnWh9WBZ8
These master passwords, and also the Hive keys themselves, are quite reminiscent of e.g. Bitcoin private keys. This type of password/key might be cryptographically robust, but they are not paper-friendly, meaning they are not easy to write to paper and read, because errors are very likely.
In this sense, I'm of the opinion that the new "master password" system adopted by InLeo (https://inleo.io/) for accounts created by @leo.voter is very beneficial. Instead of using random strings, new accounts are created with BIP-39 24-word seed phrases as "master passwords". This allows users to write the password to paper, which was not realistically feasible using the random string model. For most people, this is likely the best way to store their master password, and for this exact reason the seed phrases and the BIP-39 standard and derivatives became ubiquitous in crypto. I think all Hive services should adopt this model for master passwords.
With all that said, what do we Hive users already have available for use?
[in addition to the websites mentioned above]
One can generate random seed phrases, even offline, using Ian Coleman's tool (https://iancoleman.io/bip39/).
One can derive key pairs using @good-karma 's "Hive offline key generator" (https://feruzm.github.io/offline-keys/src/index.html) (which I used several times, I'm grateful for him to have made it available).
And as recently as last month (after I began working on the new tools) I learnt of @reazuliqbal 's "Hive Account Recovery" page (https://reazuliqbal.com/HiveAccountRecovery/), which doesn't offer key derivation but can be used to broadcast an "Account Update" operation without exposing private keys.
I should note, no tool available so far (as far as I'm aware) allows users to use more than one owner key to compose owner authority, which could be useful to add extra flexibility to security management, particularly for accounts owned by a company or a family.
Initially my intention was merely to learn to build transactions to edit an account's authorities, particularly the Owner (which is the omnipotent one), for my own personal use. Then I realised the Hive community could benefit from having better tools available for use.
Lo and behold, you are about to witness the results of my very first contact with programming. What could possibly go wrong?
Enough of introductions, let's see what came out of all this.
https://hassemer-g.github.io/keys/
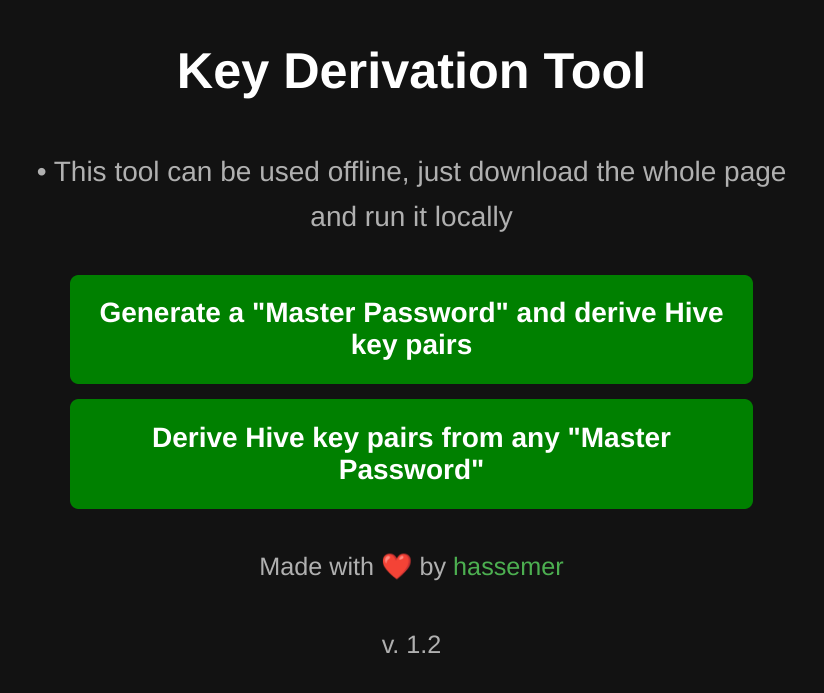
What can this tool do?
My Key Derivation Tool actually consists of two tools, each accessible from a distinct button, as per the image above. The first tool is a complete generate-and-derive tool, whereas the second one is a simpler derivation-only tool.
Let's have a look at the first, "Generator" tool:
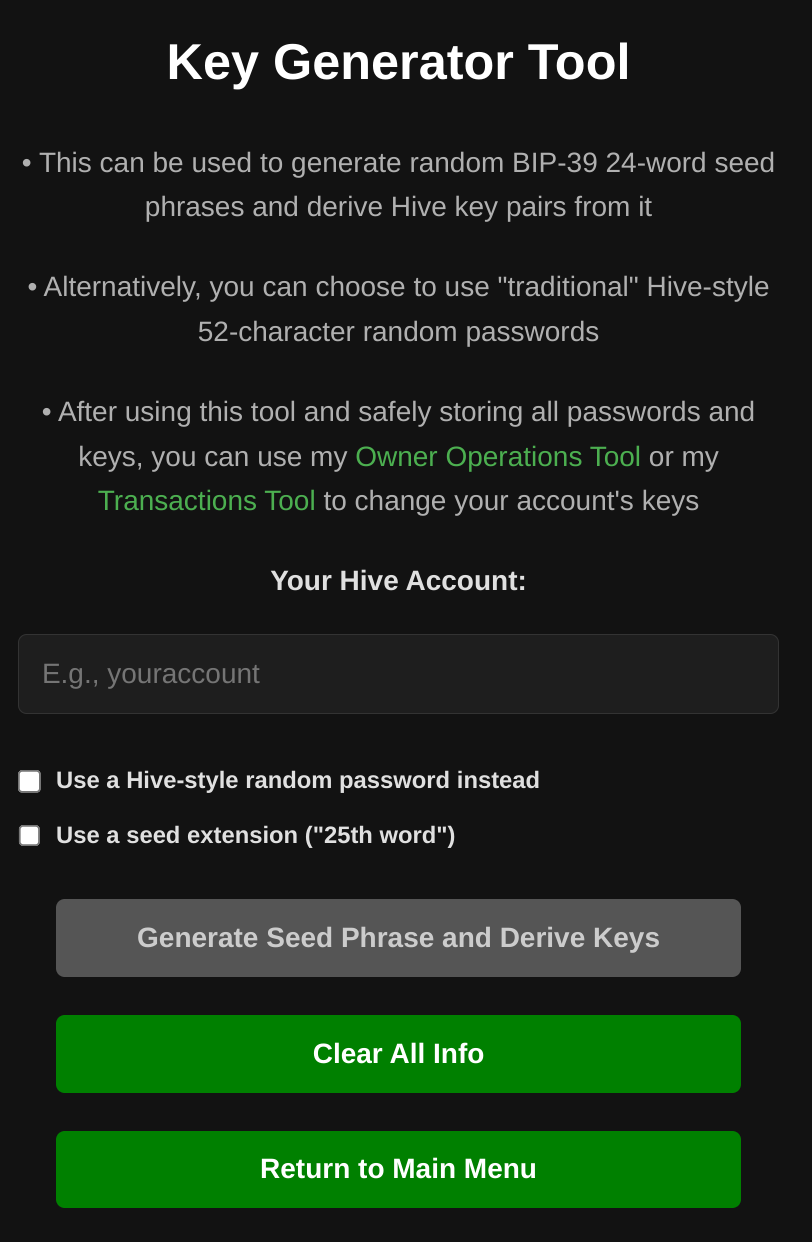
Features and functionalities:
• Generate random BIP-39 24-word seed phrases to be used as "master passwords"
• Alternatively, the user can choose to generate random Hive-style 52-character passwords
• Optionally, the user can choose to use a seed extension ("25th word"), which can be used in some security setups to add extra flexibility to key/password management
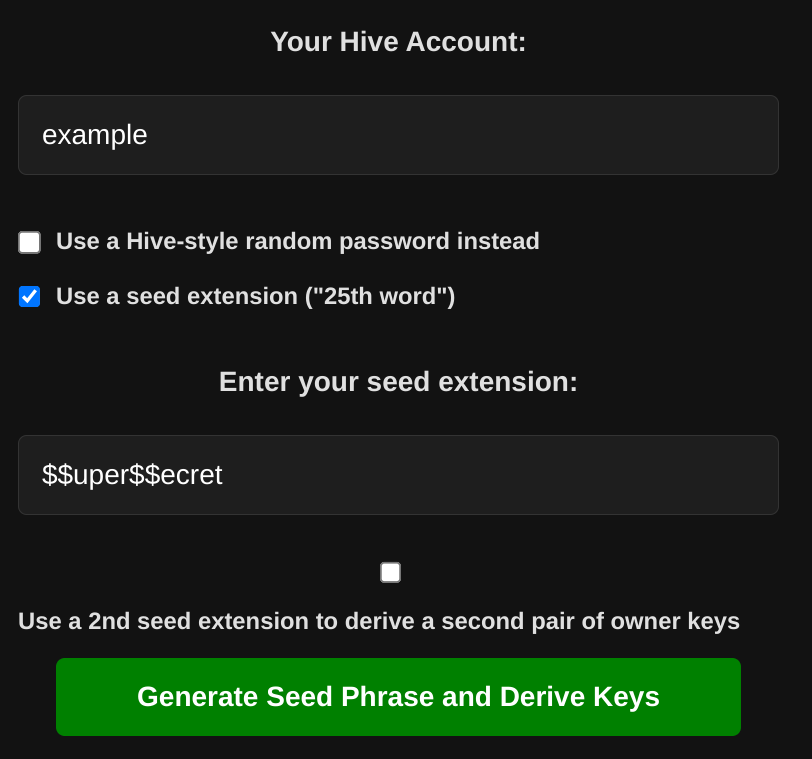
• With the master password structure chosen by the user, the tool derives all 4 Hive key pairs (here shown only the Owner Keys, the rest of them come below)
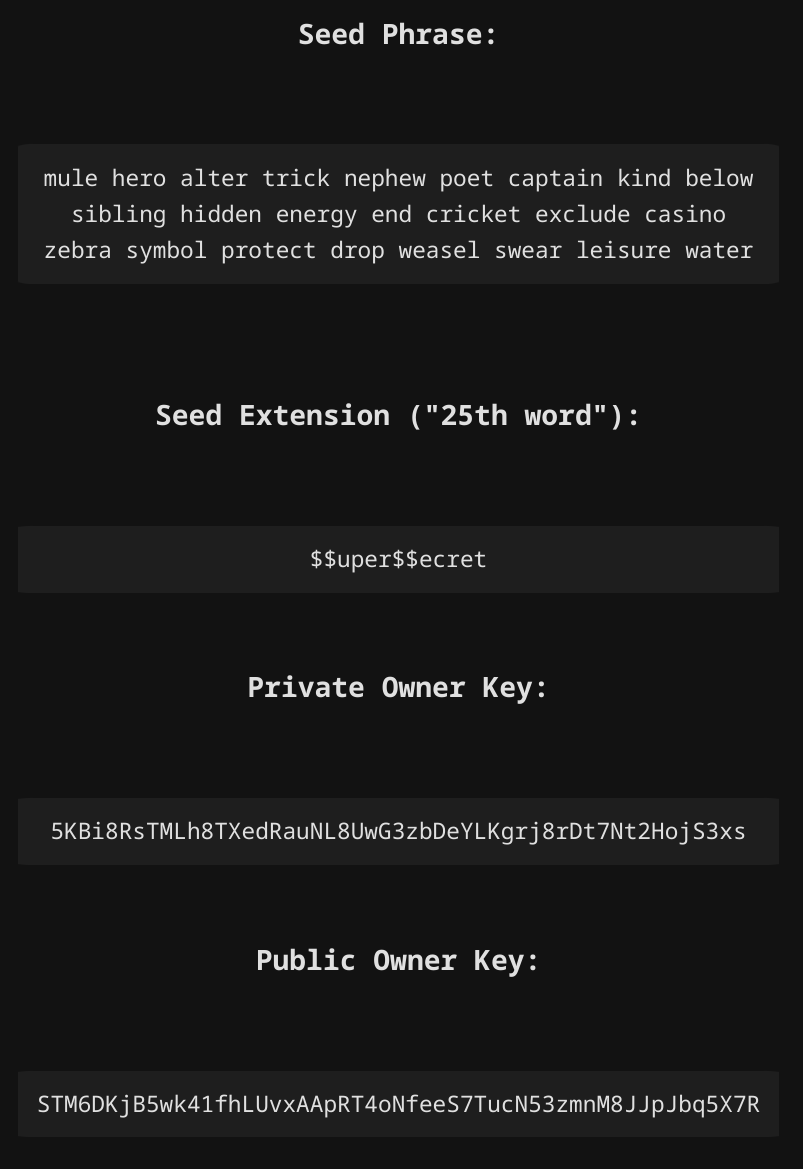
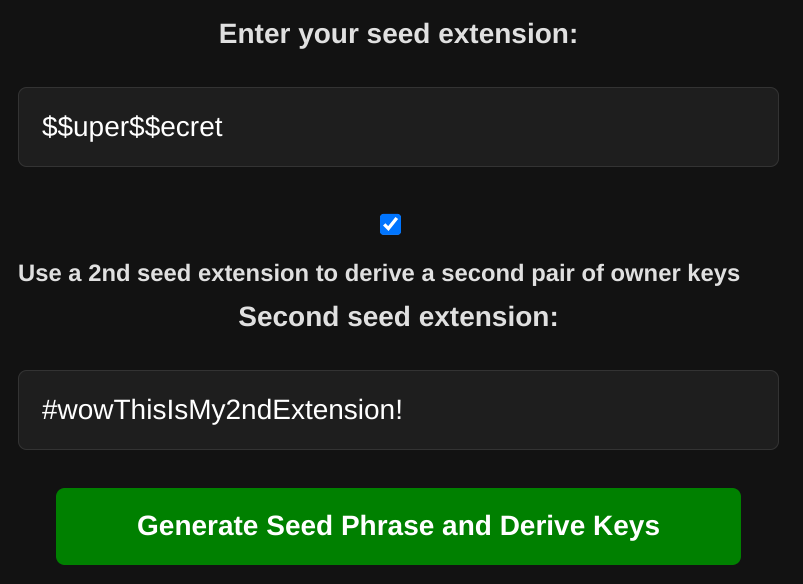
• If the user is paranoid enough, he can opt to use a second seed extension (must be different from the first extension), which will be appended to the seed phrase and used to derive a second pair of Owner Keys (which can be used in all tools in my Owner Operations Tool—to be presented here soon!)
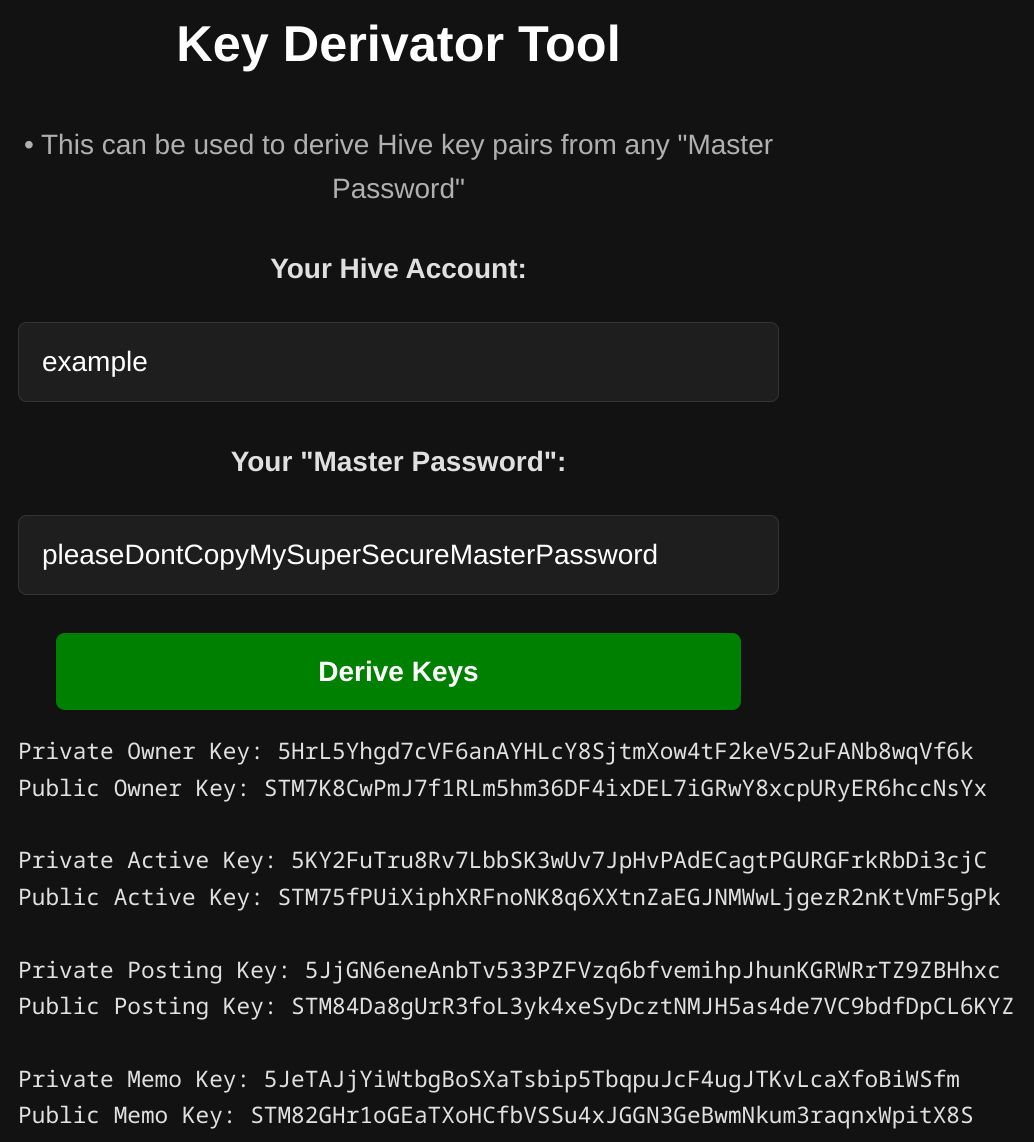
The other tool, the "Derivator-only" tool is simpler and doesn't warrant extensive explanation. It's quite straightforward, the user inputs his account name and any master password, and the tool derives all 4 key pairs. This is especially useful when one already has his master password (e.g., written on paper) and wants to retrieve his keys.
I intentionally made the results of this tool simpler, to make them easier to be copied as a whole. They arguably don't look so nice as the results of the other tool, but they're much easier to manage.
Other features:
• Mobile-friendly
• Works perfectly while offline (actually that's the ideal condition, for security reasons)
• I included all scripts in the HTML file so the page can be downloaded and run also on mobile devices (this works on Android; from what I could test, the only way to run the page on iOS is accessing it online; have I already said how much I dislike iOS?)
Please, let me know if you find any bugs! I tested these tools thoroughly, but I'm only human and errors might have been overlooked!
And that's it for today friends! In my next posts I will present the other tools I built, and also present updates on how the project to introduce more people to Hive (see my previous post) is coming along. Stay tuned!