Problem Statement- In an era of heightened security concerns, the need to efficiently manage and respond to suspicious architecture and movement near borders is paramount. However, the current communication protocols often result in significant delays in taking appropriate actions, leading to potential security breaches. Therefore, there is a pressing need to develop a solution that saves communication time for effectively addressing and mitigating threats posed by suspicious architecture and movement near border areas.
Idea Proposed- Integrating cross-border architecture detection and corresponding inventory updates into the realm of global defense.
**Aim... **
The project aims to address security concerns near borders by improving communication protocols to efficiently manage and respond to suspicious architecture and movement. Current protocols often cause delays in taking appropriate actions, risking security breaches. The goal is to develop a solution that minimizes communication time, allowing for swift and effective response to potential threats.
Features...
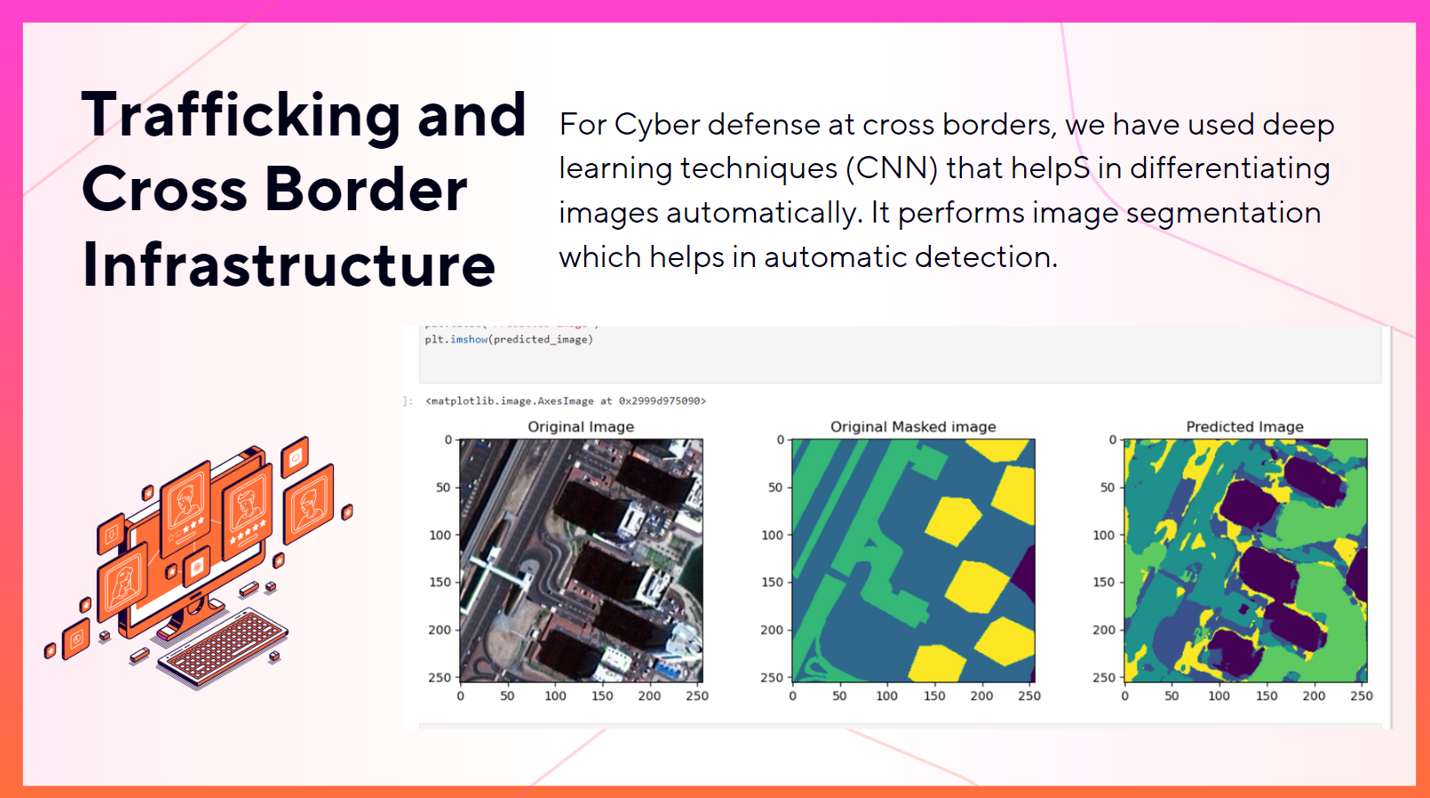
The system employs Deep Learning models for satellite image analysis, leveraging OpenCV for computer vision tasks. It detects cross-border suspicious activities by analyzing satellite imagery for anomalies, such as unauthorized border crossings or unusual movements. OpenCV assists in image preprocessing, feature extraction, and pattern recognition. By integrating these technologies, the system can identify potential threats along borders with high accuracy and speed, enabling prompt response from defense authorities.
What are system employees...
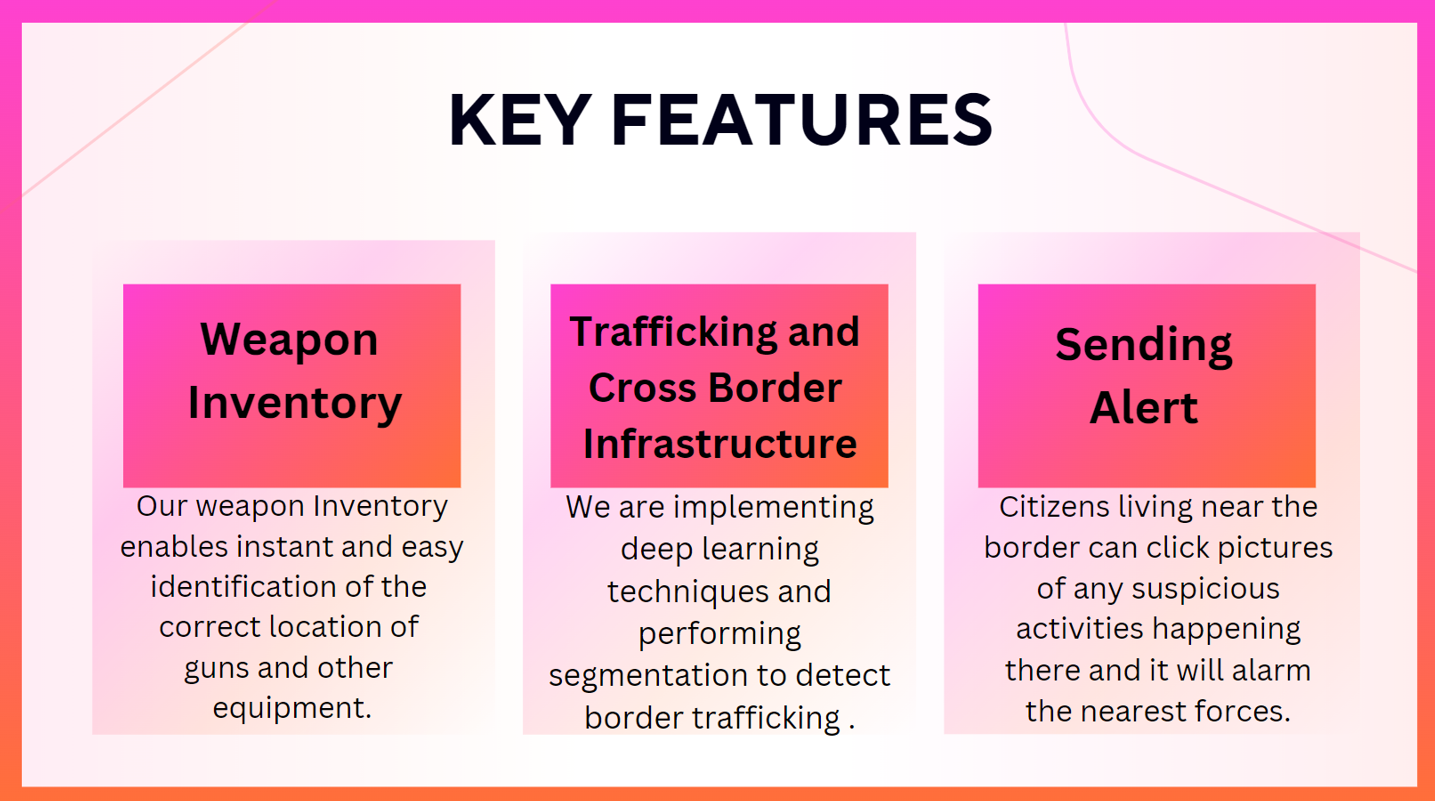
- The system employs Deep Learning models for satellite image analysis, leveraging OpenCV for computer vision tasks. It detects cross-border suspicious activities by analyzing satellite imagery for anomalies, such as unauthorized border architecture or unusual movements. OpenCV assists in image preprocessing, feature extraction, and pattern recognition. By integrating these technologies, the system can identify potential threats along borders with high accuracy and speed, enabling prompt response from defense authorities. We also generate the query by locals upon seeing unusual movement and for quick action.
The system integrates Deep Learning models for satellite image analysis, utilizing OpenCV for computer vision tasks. It detects cross-border suspicious activities by scrutinizing satellite imagery for anomalies like unauthorized border architecture or unusual movements. OpenCV aids in image preprocessing, feature extraction, and pattern recognition. This amalgamation enables the system to pinpoint potential threats along borders swiftly and accurately, facilitating rapid response from defense authorities. Additionally, the system incorporates a feature allowing locals to generate queries upon observing unusual movements, expediting action.
The system integrates Deep Learning models for satellite image analysis, leveraging OpenCV for computer vision tasks. It detects cross-border suspicious activities by scrutinizing satellite imagery for anomalies like unauthorized border architecture or unusual movements. OpenCV aids in image preprocessing, feature extraction, and pattern recognition. This amalgamation enables the system to pinpoint potential threats along borders swiftly and accurately, facilitating rapid response from defense authorities. Additionally, the system incorporates a feature allowing locals to generate queries upon observing unusual movements, expediting action. Furthermore, it automatically updates ammunition inventories to ensure readiness for effective defense measures.
Outcomes-
High Resolution and Coverage: Satellite imagery can provide high-resolution views of large geographic areas, allowing for comprehensive coverage of border regions. This enables detailed monitoring and detection of suspicious activities over vast expanses of terrain, which might not be feasible with radar systems alone.
Anomaly Detection: Deep Learning models trained on satellite imagery can learn to identify subtle anomalies indicative of suspicious activities, such as unauthorized border architecture or unusual movements of people or vehicles. This capability enhances the system's ability to detect potential threats with a high degree of accuracy, even in complex and dynamic environments.
Multi-Spectral Analysis: Satellite imagery often includes data across multiple spectral bands, providing valuable information beyond what radar systems can offer. This includes insights into vegetation health, land use changes, and other environmental factors that can aid in identifying potential threats and understanding their context.
Cost-Effectiveness: While radar systems can be effective for certain surveillance tasks, they can also be expensive to deploy and maintain, particularly over large border areas. Leveraging existing satellite infrastructure for surveillance purposes can offer a more cost-effective solution, especially when combined with Deep Learning algorithms that can automate much of the analysis process.
Timely Updates and Response: By integrating a feature that allows locals to generate queries upon observing unusual movements, the system facilitates rapid reporting of suspicious activities to authorities. This can significantly reduce response times and enhance the effectiveness of defense measures.
Ammunition Inventory Management: The automatic updating of ammunition inventories ensures readiness for effective defense measures, providing an additional layer of preparedness in response to detected threats.

**Future Scope- **
Enhanced Detection Algorithms: Continuously refine and improve the algorithms used for detecting architecture across borders. This could involve incorporating machine learning techniques to better identify and classify architectural styles accurately.
Geographical Expansion: Extend the project's coverage to include more regions and countries around the world. This expansion could involve collaborating with local architectural experts and organizations to gather data and insights into various architectural styles.
Real-Time Inventory Updates: Implement mechanisms for real-time inventory updates. This could involve integrating with architectural databases or leveraging crowdsourcing to gather information about architectural changes and updates.
Data Visualization Tools: Create interactive data visualization tools to help users explore and analyze architectural data more effectively. This could include maps, charts, and graphs that highlight trends and patterns in architectural styles across different regions.
Sustainability Integration: Expand the project's scope to include sustainability considerations in architectural analysis. This could involve identifying and promoting sustainable architectural practices and highlighting buildings and structures that incorporate green design principles.
Team Name-
Hacker Log
Team Members-
Sahil Gupta
Utkarsh Mohan
Utkarsh Baliyan
Yatiraj Upadhyay
Event-
Vihaan 007 at DTU